 Summary. The world’s largest data heist and hacking campaign was recently discovered and it is still underway. There are a surprisingly small number of news reports about this story so far. According to a report by PC World, the Kneber botnet virus “puts the potential threat of last year’s Conficker worm to shame.” According to an article published by InformationWeek, “this botnet makes Operation Aurora, the cyber attack directed at Google and 33 other companies last December, look insignificant.”
Summary. The world’s largest data heist and hacking campaign was recently discovered and it is still underway. There are a surprisingly small number of news reports about this story so far. According to a report by PC World, the Kneber botnet virus “puts the potential threat of last year’s Conficker worm to shame.” According to an article published by InformationWeek, “this botnet makes Operation Aurora, the cyber attack directed at Google and 33 other companies last December, look insignificant.”
Overview. On 18 February 2010, a full report [PDF] published by NetWitness.com disclosed the following details about the 18-month long hacking campaign:
- More than 75,000 computers at 2,500 companies and government agencies world-wide have been compromised
- A single 75GB cache of data stolen over a span of just one month included 68,000 corporate login credentials as well as user login data for Facebook, Yahoo, and Hotmail. Also included were 2,000 SSL certificate files.
- At least 196 countries have been attacked in this campaign which has been one of the broadest reaching campaigns in history encompassing numerous world languages and going beyond geo-political boundaries.
- Seemingly independent rogue criminal hacker gangs are working together to install more than one virus per computer in an effort to ensure sustainability. If one threat is removed, the other can reinstall it.
- There is now “evidence supporting the existence of a large and dispersed criminal enterprise.”
- The ultimate implications of these undetected data losses and infestations of public and commercial organizations are far-reaching and complex and transcend simple labels.
“The widely deployed security technologies modern enterprises use to protect themselves such as firewalls, antivirus and intrusion detection technologies, even when well managed, are ineffective in countering the current and ongoing threat to our information systems posed by a focused criminal adversary or nation-state. … This is due to the criminal hacker element being aware of the limitations of these technologies and engineering their exploits and malware around them.” ~ NetWitness.com Report, 17 February 2010
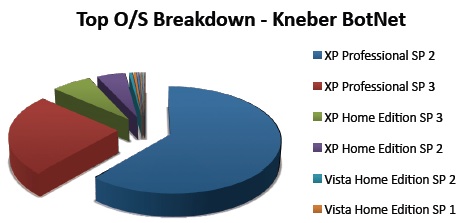
Analysis by Operating System. Below is a chart showing the Kneber Botnet Virus attack by operating system. A simplistic analysis of this chart would suggest that XP Professional SP2 is the most vulnerable. However, the larger number of XP Professional computers hacked is simply a reflection that businesses were targeted more than home computers.
What You Can Do. Here are some suggestions for making your computing life more secure.
- Buy an Apple Computer. This historic data heist that impacted many businesses in 196 countries shows that even when a broad spectrum indiscriminate attack is launched, Apple computers seem to be a safer and more secure computing platform. The Kneber Botnet virus was written for Windows computers only. IT professional should consider using Apple Servers for mission critical and confidential data systems.
- Use an Apple iPhone. In addition to the stability and security of Apple desktop computers, the Apple iPhone is even more secure because the phone can be configured to be erased automatically after 10 failed login attempts. The phone can also be erased remotely in the event it’s lost, and the GPS system can be used to help track down the phone. Read more…
- Use an Encrypted Database. The most secure method of storing information would be to use an encrypted database to store your financial, identity, and password information. If this encrypted database software is on an iPhone, then it provides an extra measure of security. Products such as CallPod Keeper will securely store your data, and if someone attempts to hack into the data vault, after three failed attempts the data is destroyed (so make sure you have a backup). Read more…
- Use Different Complex Passwords. If you plan to memorize all of your passwords, you’ll probably pick a simple password (or system) and use it everywhere. The problem with this is that once a person has one password, they are, in effect, given the key to all your passwords. It’s best to use very different passwords with every system and use only complex passwords. To have 30 or 40 different complex passwords requires a data vault (as described in step #3 above). If you don’t want to spend the money on a data vault, then consider using a complex cypher code that only you know and change it frequently.
- Change Passwords Frequently. Your computer may be secure, but what about your bank’s computer and those used for other websites, stores, and online accounts? Hackers probably aren’t interested in accessing your home computer. What they really want is to hack into a single computer that contains hundreds or thousands of passwords. So, while the likelihood of your secured computing device getting hacked is slim, the possibility of your information being stolen from your financial institution computer is high. Changing passwords frequently ensures that once the login credentials are passed on to buyers on the black market, you will have changed the login and password by then.
- Key-logger Security. A key-logger system can track what you are typing. However, if your login credentials are saved (securely) and automatically entered, this will prevent a key-logger from knowing what they are. You would obviously need to do this before having an infection.
- Travel Precautions. Erase your cell phone data, iPhone, and notebook prior to travel or have travel designated devices. Read more in this PDF unclassified government report.
- Clean System Images. Consider occasionally erasing your entire computer and restoring a known good backup image of the entire computer using software such as Acronis True Image 2010.
Video. Below is a video of Gregory Johnson discussing this security breach.
Document History. This document was first published on 20100218th1311. Additional information was added at 201018th1839. This document was updated on 20100219fr1012.